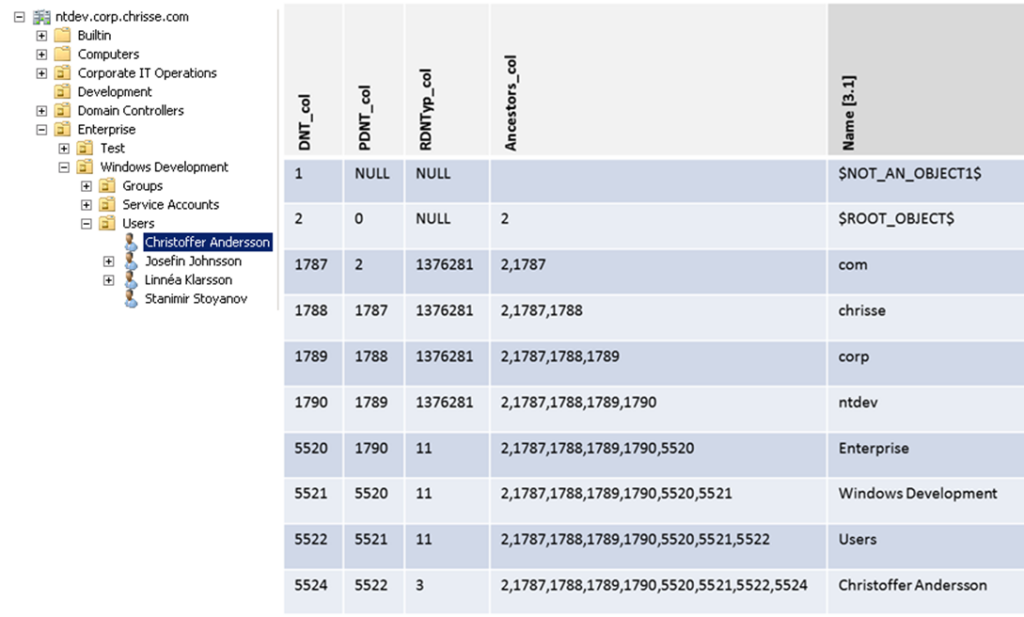
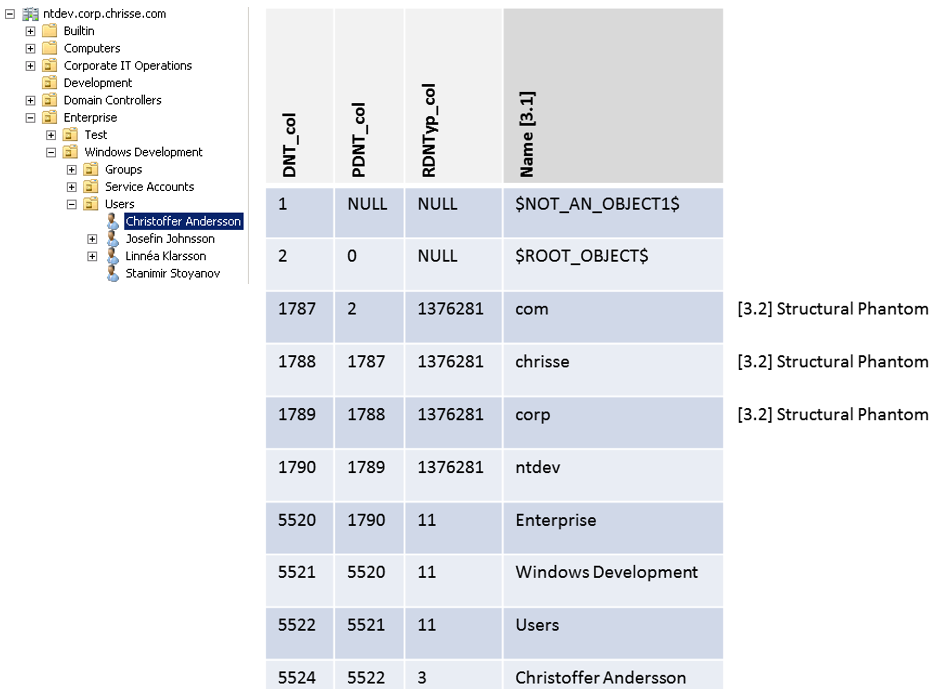
Yesterday when I was researching the new Windows Server 8 Beta bits I did a discovery of a new operational attribute [1] – dumpReferences (that I haven’t seen documented anywhere)
So what does “dumpReferences” really do? It works similar to the “dumpDatabase” operational attribute, but instead it finds all none-linked (simple) references to a given objects [2] DNT (Distinguee Name Tag)
[1] List of operational attributes in previous Windows Server releases: http://msdn.microsoft.com/en-us/library/cc223297(v=prot.10).aspx.
[2] If you want to know how DNTs work have a look at: http://blogs.chrisse.se/2012/02/15/how-the-active-directory-data-store-really-works-inside-ntds-dit-part-2
So how do you play with this?
Table 1: dumpReferences
|
LDIF Sample |
|
dn: changetype: modify add: dumpReferences dumpReferences:<DN to dump references of> |
Let’s try an example
We create two users with the following DNs:
- CN=Lena Andersson,CN=Users,DC=wtf,DC=nttest,DC=chrisse,DC=com
- CN=Elina Andersson,CN=Users,DC=wtf,DC=nttest,DC=chrisse,DC=com
Now set the “Se-Also” attribute on “CN= Lena Andersson,CN=Users,DC=wtf,DC=nttest,DC=chrisse,DC=com” to a value of “CN=Elina Andersson,CN=Users,DC=wtf,DC=nttest,DC=chrisse,DC=com”
Let’s dump the references to in the DIT to “CN=Elina Andersson,CN=Users,DC=wtf,DC=nttest,DC=chrisse,DC=com” now – I choose to do this with LDP.exe
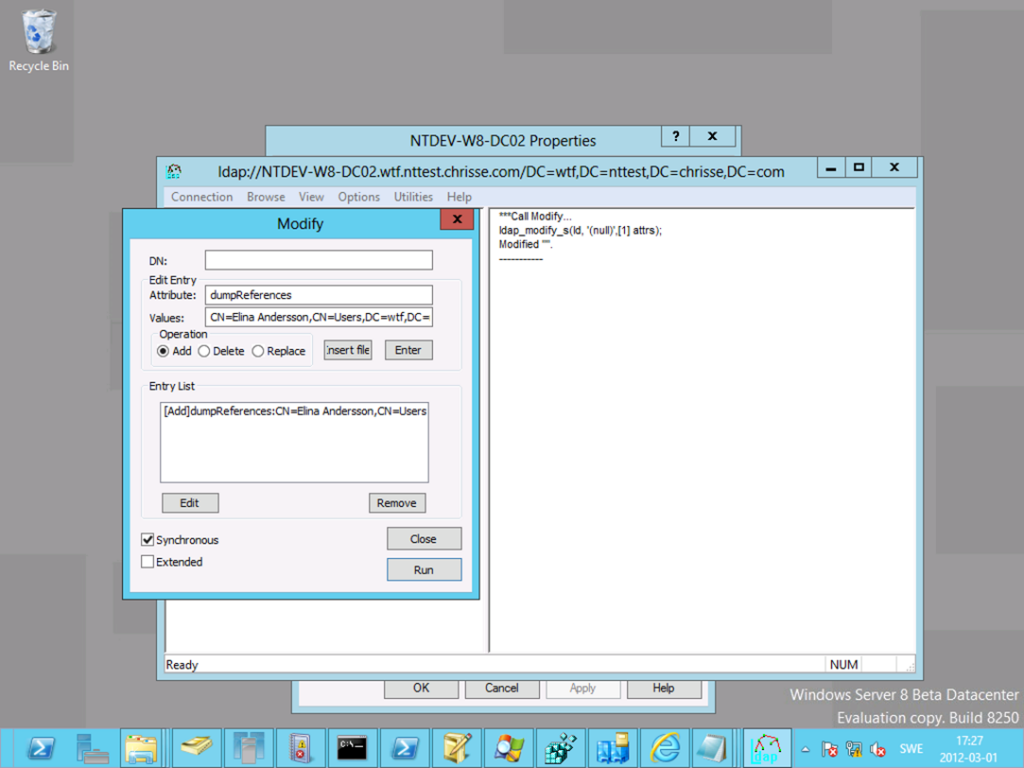
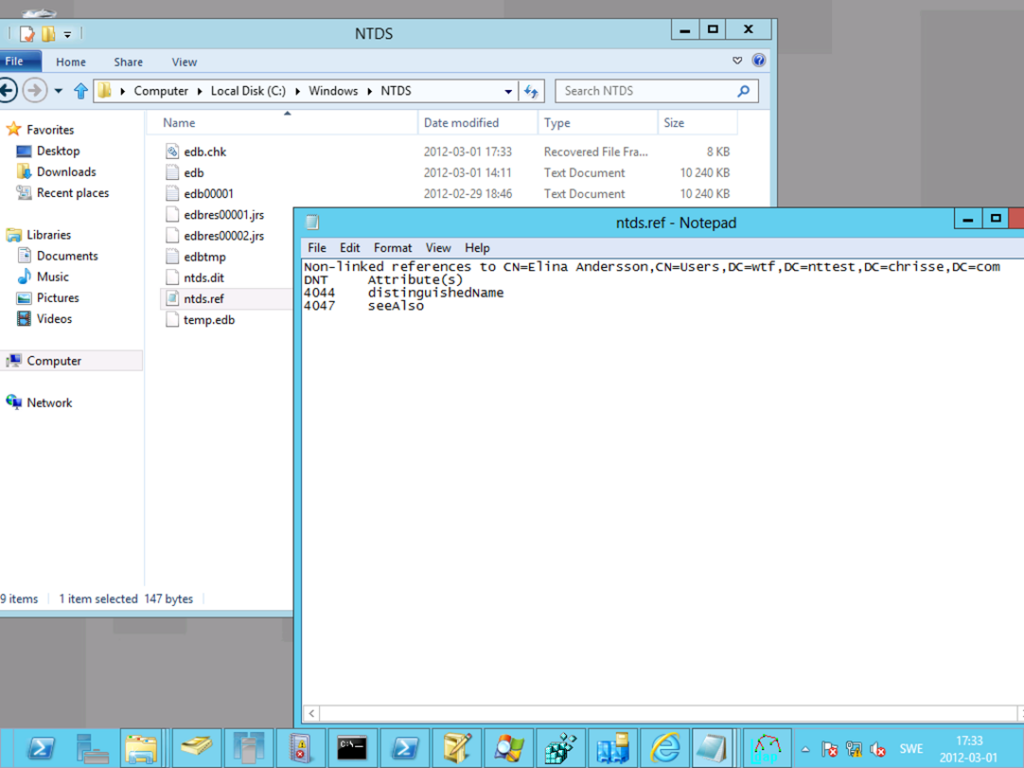
Now go into the path where you store [3] the NTDS.dit database on the DC you executed the above operation against and you should find a “NTDS.ref” file open it in your preferred text editor and you can know see the DNTs of all object’s refereeing to “Elina” and by which attribute.
DNT: 4044 is representing the object of “Elina” itself as all objects references them self
DNT: 4047 is representing the object of “Lena” that is referencing “Elina” in the “see-Also” attribute
[3] You can find the path by looking at “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters\DSA Database File”
Summary
I don’t see any value of this actually and maybe this is something left in this release for development and testing purposes so it might disappear in the final release – How did I find this one? Well that qualifies for a post by its own to explain all tests I perform on a new Windows build J